Create a Shakudo Service Account with Custom Image Pull Secret
This guide creates a Service Account in the hyperplane-pipelines namespace and mounts an image pull secret (Kubernetes secret-based authentication) so Pods can pull private images.
You can use hyperplane-jhub namespace if you wish to use it in Sessions for development.
Here is how purposes are mapping into namespaces:
Development: hyperplane-pipelines
Workloads: hyperplane-jhub
Prerequisites
- Permissions to create secrets, and service accounts.
- An existing private repository with images to pull.
1 Create a service account
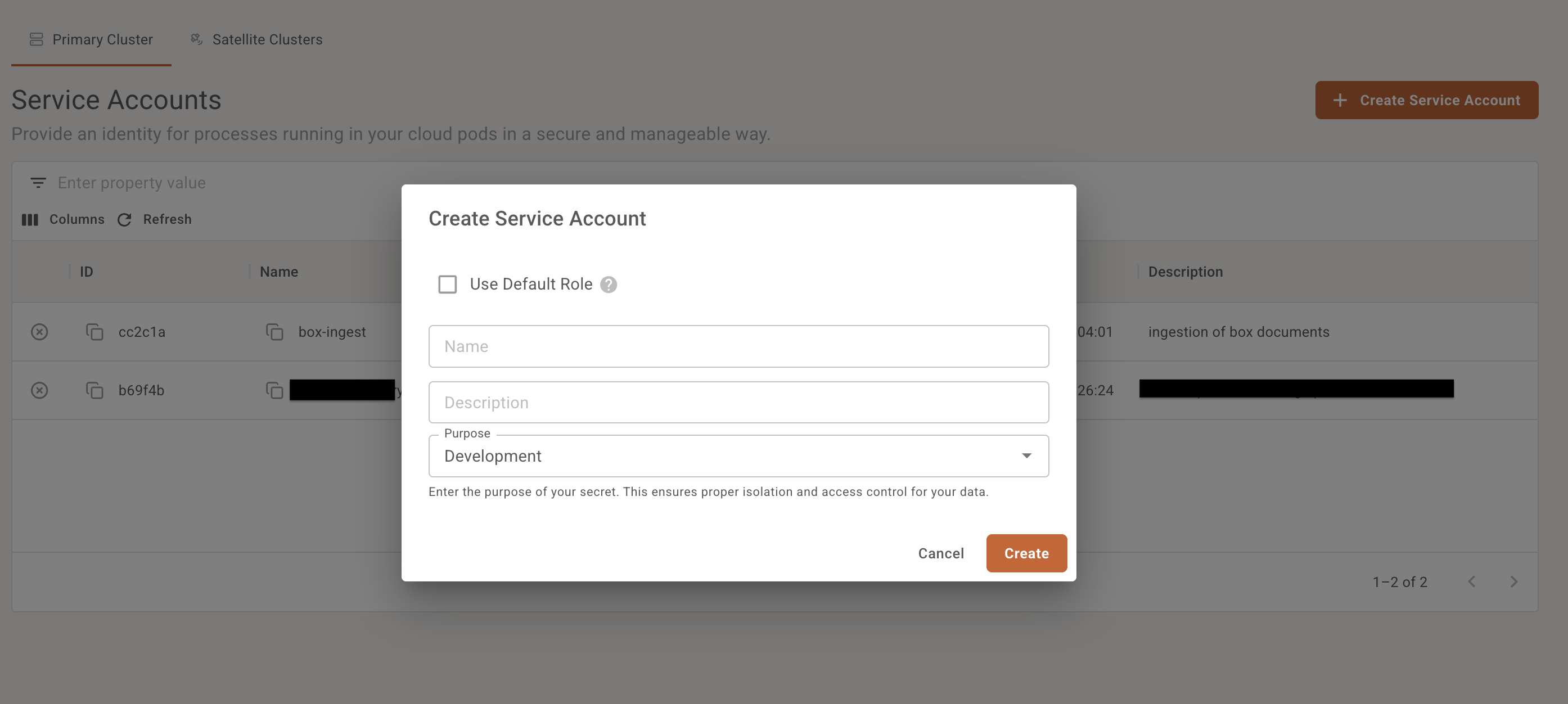
The name can be hyperplane-pipelines-sa as an example.
Following steps will be finished in Shakudo cloud terminal.
![]()
2 Set variables
NS=hyperplane-pipelines
SA_NAME=hyperplane-pipelines-sa
PULL_SECRET_NAME=ecr-pull-secret
3 Create the image pull secret
Create a docker-registry secret using your existing username password.
kubectl create secret docker-registry "$PULL_SECRET_NAME" \
--docker-server="$PRIVATE_REGISTRY" \
--docker-username=username \ # This should be your username
--docker-password-stdin \
-n "$NS"
If the secret exists and you need to refresh the token, delete and recreate it:
kubectl delete secret "$PULL_SECRET_NAME" -n "$NS" --ignore-not-found
kubectl create secret docker-registry "$PULL_SECRET_NAME" \
--docker-server="$PRIVATE_REGISTRY" \
--docker-username=username \ # This should be your username
--docker-password-stdin \
-n "$NS"
4) Patch the Service Account and attach the imagePullSecret
kubectl patch serviceaccount "$SA_NAME" -n "$NS" \
-p "{\"imagePullSecrets\":[{\"name\":\"$PULL_SECRET_NAME\"}]}"
5) Verify
kubectl get sa "$SA_NAME" -n "$NS" -o yaml | grep -A2 imagePullSecrets
You should see the secret name under imagePullSecrets.
6) Use the Service Account in your workloads
Reference the Service Account so Pods inherit the pull secret.
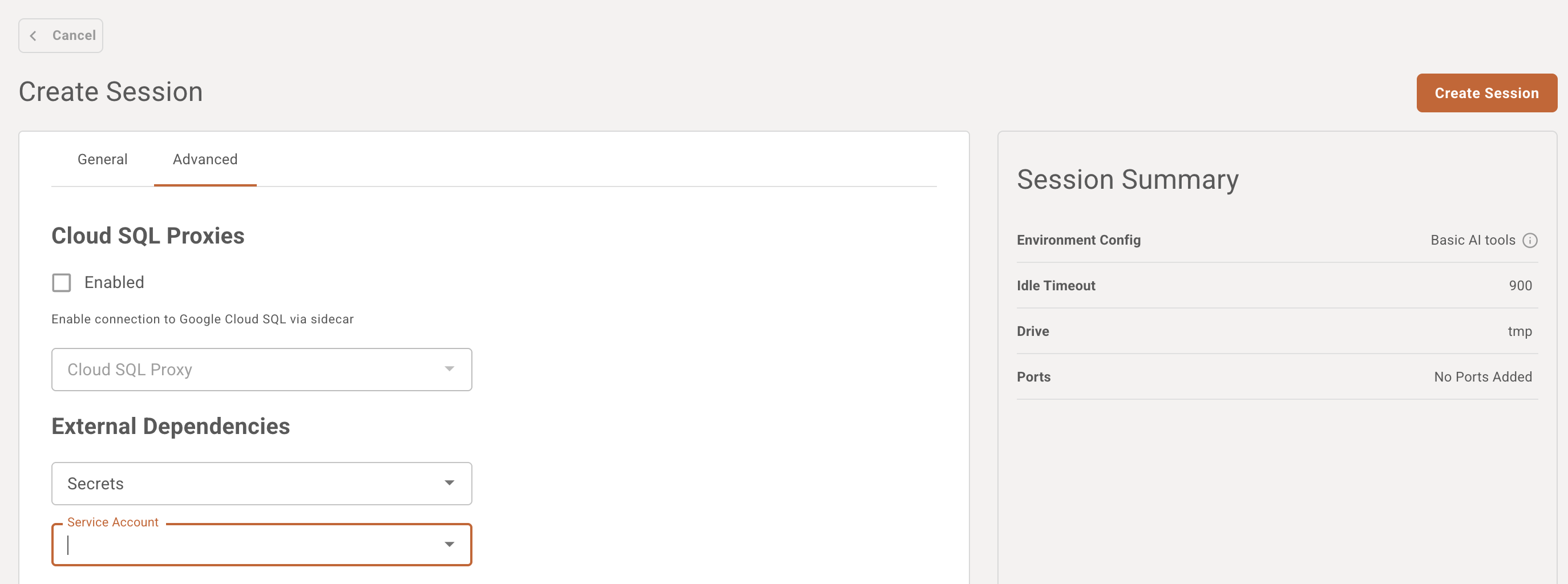
(Optional) Attach the pull secret to the default Service Account, to allow every pod within the namespace be able to pull the images by default.
kubectl patch serviceaccount default -n "$NS" \
-p "{\"imagePullSecrets\":[{\"name\":\"$PULL_SECRET_NAME\"}]}"
Troubleshooting
ImagePullBackOff/ErrImagePull:- Secret must exist in the same namespace as the Pod.
- Ensure
--docker-servermatches your custom registry. - Check image URI correctness and repository permissions.